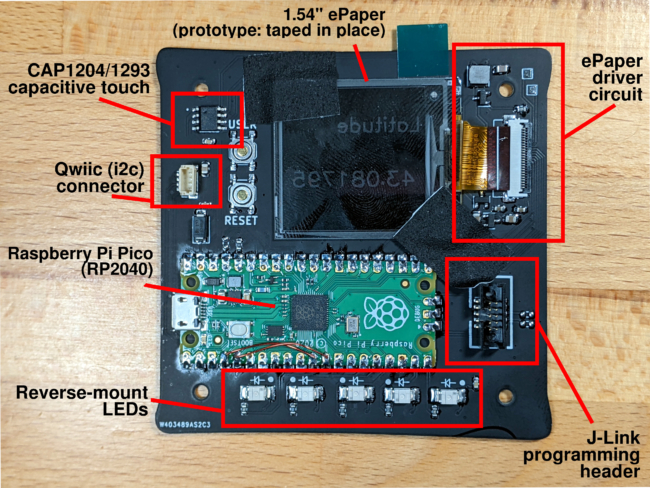
We are excited to announce the general availability of two new output stream destinations: MongoDB Time Series and InfluxDB. With Golioth, you can now stream your IoT device data directly into these popular databases, eliminating the need for additional backend APIs to ingest data. This expands your integration possibilities with Golioth, bringing more flexibility and efficiency to your IoT data handling.
Why MongoDB Time Series and InfluxDB?
As an enabler of a broad range of IoT applications, Golioth understands the diverse requirements of various remote sensing applications. Sensor data, by nature, is time series data – it’s collected at regular intervals and is most valuable when observed over time for trends and patterns.
MongoDB Time Series and InfluxDB are databases specifically designed for this kind of data.
MongoDB Time Series is a powerful extension of MongoDB, specifically tailored for time-series data. Its strength lies in its built-in capabilities for handling large-scale, high-throughput, and complex querying scenarios. With this, storing and analyzing time-series data becomes effortless, making it ideal for IoT use cases.
InfluxDB, on the other hand, is a high-performance data store purpose-built for time-series data. It stands out for its support for high throughput ingest, compression, and real-time querying. This makes InfluxDB particularly suited to handle the high write and query loads commonly associated with large IoT deployments.
Expanding Your IoT Data Integration Possibilities
At Golioth, our goal is to streamline the path from idea to deployment in IoT development. The addition of MongoDB Time Series and InfluxDB to our output streams is a major milestone, enhancing the way you can route your IoT data directly to your preferred databases.
If you’re already using MongoDB Time Series or InfluxDB, this update allows for a seamless flow of information from your IoT devices to your databases, unifying your tech stack and simplifying your development experience.
With the incorporation of these new output streams, we’re supporting a broader spectrum of use cases and accelerating the journey from prototype to production.
Learn More about the New Output Streams
You can get started with MongoDB Time Series and InfluxDB output streams by following the guides in our documentation:
To understand more about output streams, how they work, and why they’re beneficial to your IoT projects, take a look at our previous post on output streams.
Need Help or Want More Database Support?
If you have any questions or need help getting started with MongoDB Time Series or InfluxDB output streams, don’t hesitate to reach out on our community forum. Our team and fellow Golioth users are there to help you.
If you’re using a different database and would like to connect it to Golioth, please let us know at [email protected]. Your feedback will help us prioritize support for other database output streams in the future.
We’re excited to see what you build with these new capabilities. As always, we’re here to support your IoT journey. Your feedback and questions are always welcome.
Happy building!