Managing device identity securely at scale is one of the hardest challenges in IoT. Certificates expire, credentials need to be rotated, and operational complexity often forces teams to choose between security best practices and shipping products on time.
Today, we’re excited to announce a major step forward: External Public Key Infrastructure (PKI) provider integration in Golioth, starting with support for AWS Private Certificate Authority (Private CA). This new capability enables devices to perform certificate rotation directly through the Golioth Device API, dramatically simplifying secure device lifecycle management.
Why Certificate Rotation Matters
Golioth supports two device authentication methods: Pre-Shared Keys (PSKs) and X.509 certificates. While PSKs can be appropriate for early development and constrained use cases, short-lived certificates are the recommended approach for production deployments.
The reason is simple: PSKs are static secrets. If a PSK is ever extracted from a device, leaked from a manufacturing system, or reused across devices, there is no clean way to limit the blast radius without manually replacing credentials, which often requires physical access to devices already in the field.
Short-lived certificates dramatically reduce this risk:
- Compromise is time-bounded: Even if a certificate is exposed, it automatically expires.
- No shared secrets: The device’s private key never leaves its secure hardware module.
- Routine rotation becomes normal rather than exceptional.
- Revocation and recovery are built into the model.
In other words, certificate rotation shifts security from a “hope it never leaks” posture to a “assume compromise and limit impact” strategy, which is the foundation of modern, large-scale IoT security.
Until now, many teams stuck with PSKs not because they were more secure, but because certificate rotation was operationally hard. With Golioth’s new hosted PKI integration, that trade-off disappears.
What’s New: Hosted PKI Integration
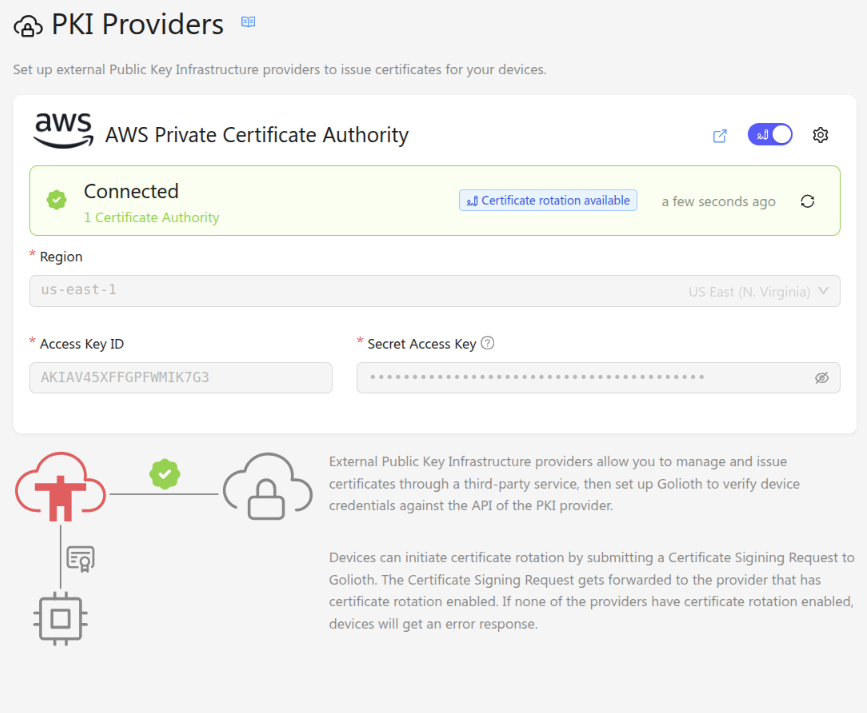
From today, Golioth supports integration with external, hosted PKI providers, allowing Golioth to maintain an automatically updated list of Certificate Authority certificates for your project. The integration also supports issuing device certificates through Golioth’s device API, enabling seamless certificate rotation for your devices in the field.
For the initial launch, Golioth integrates with AWS Private CA, a fully managed certificate authority service from AWS. We have designed the external PKI integration to be extensible, and we plan to add support for other hosted PKI providers in the near future.
How It Works
At a high level, the certificate rotation workflow looks like this:
- A device running the Golioth Firmware SDK initiates a certificate rotation request.
- Golioth securely brokers the request to the configured external PKI provider.
- A new device certificate is issued by the external PKI provider (e.g. AWS Private CA)
- Golioth sends the new certificate to the device, which can install and start using it without any downtime.
All of this happens using Golioth’s existing infrastructure, allowing certificate rotation to happen securely, without the need for glue code, custom services, or bespoke provisioning pipelines.
What’s Next?
While AWS Private CA is the first supported provider, we plan to add support for other hosted PKI providers in the near future. We will also be partnering with silicon vendors to offer secure provisioning services. With Golioth’s unified certificate rotation API, you should be able to choose the PKI provider that fits your organization, without changing your device firmware or security model.
Let us know which PKI providers you would like to integrate with to simplify your certificate management!
Get Started Today
If you’re already using Golioth, you can start experimenting with hosted PKI-backed certificate rotation today using the Golioth Firmware SDK and AWS Private CA.
- Read how to set up your integration in our documentation
- Try our Certificate rotation firmware example
Security shouldn’t require extra infrastructure or custom code, and with seamless certificate rotation, we believe building a secure products will be a little easier.


No comments yet! Start the discussion at forum.golioth.io